we provide Actual Fortinet NSE4_FGT-6.4 exam question which are the best for clearing NSE4_FGT-6.4 test, and to get certified by Fortinet Fortinet NSE 4 - FortiOS 6.4. The NSE4_FGT-6.4 Questions & Answers covers all the knowledge points of the real NSE4_FGT-6.4 exam. Crack your Fortinet NSE4_FGT-6.4 Exam with latest dumps, guaranteed!
Online Fortinet NSE4_FGT-6.4 free dumps demo Below:
NEW QUESTION 1
Which two actions can you perform only from the root FortiGate in a Security Fabric? (Choose two.)
- A. Shut down/reboot a downstream FortiGate device.
- B. Disable FortiAnalyzer logging for a downstream FortiGate device.
- C. Log in to a downstream FortiSwitch device.
- D. Ban or unban compromised hosts.
Answer: A
NEW QUESTION 2
Examine the two static routes shown in the exhibit, then answer the following question.
Which of the following is the expected FortiGate behavior regarding these two routes to the same destination?
- A. FortiGate will load balance all traffic across both routes.
- B. FortiGate will use the port1 route as the primary candidate.
- C. FortiGate will route twice as much traffic to the port2 route
- D. FortiGate will only actuate the port1 route in the routing table
Answer: B
Explanation:
“If multiple static routes have the same distance, they are all active; however, only the one with the lowest priority is considered the best path.”
NEW QUESTION 3
Why does FortiGate Keep TCP sessions in the session table for several seconds, even after both sides (client and server) have terminated the session?
- A. To allow for out-of-order packets that could arrive after the FIN/ACK packets
- B. To finish any inspection operations
- C. To remove the NAT operation
- D. To generate logs
Answer: B
NEW QUESTION 4
View the exhibit.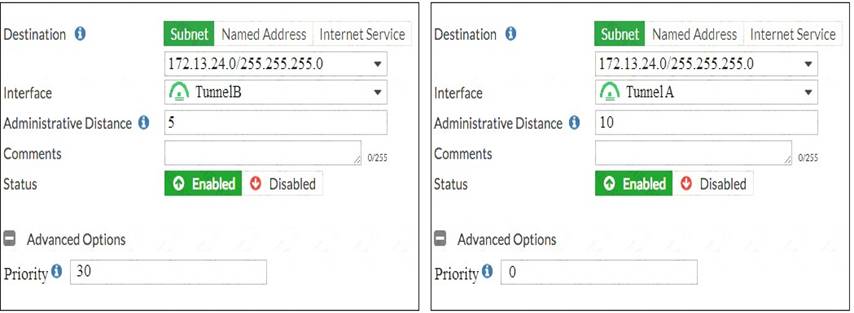
Which of the following statements are correct? (Choose two.)
- A. This setup requires at least two firewall policies with the action set to IPsec.
- B. Dead peer detection must be disabled to support this type of IPsec setup.
- C. The TunnelB route is the primary route for reaching the remote sit
- D. The TunnelA route is used only if the TunnelB VPN is down.
- E. This is a redundant IPsec setup.
Answer: CD
NEW QUESTION 5
Refer to the web filter raw logs.
Based on the raw logs shown in the exhibit, which statement is correct?
- A. Social networking web filter category is configured with the action set to authenticate.
- B. The action on firewall policy ID 1 is set to warning.
- C. Access to the social networking web filter category was explicitly blocked to all users.
- D. The name of the firewall policy is all_users_web.
Answer: D
NEW QUESTION 6
Which two settings can be separately configured per VDOM on a FortiGate device? (Choose two.)
- A. System time
- B. FortiGuaid update servers
- C. Operating mode
- D. NGFW mode
Answer: AD
NEW QUESTION 7
Which type of logs on FortiGate record information about traffic directly to and from the FortiGate management IP addresses?
- A. System event logs
- B. Forward traffic logs
- C. Local traffic logs
- D. Security logs
Answer: A
NEW QUESTION 8
Which three authentication timeout types are availability for selection on FortiGate? (Choose three.)
- A. hard-timeout
- B. auth-on-demand
- C. soft-timeout
- D. new-session
- E. Idle-timeout
Answer: ADE
Explanation:
https://kb.fortinet.com/kb/documentLink.do?externalID=FD37221
NEW QUESTION 9
Refer to theexhibits.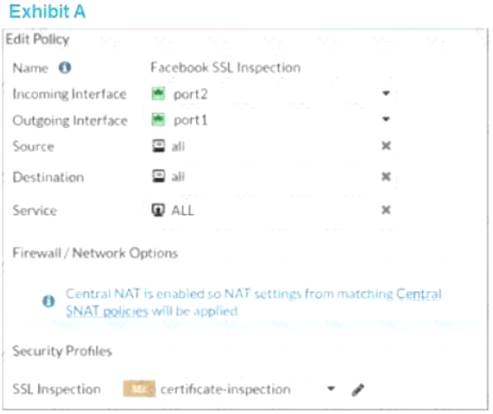
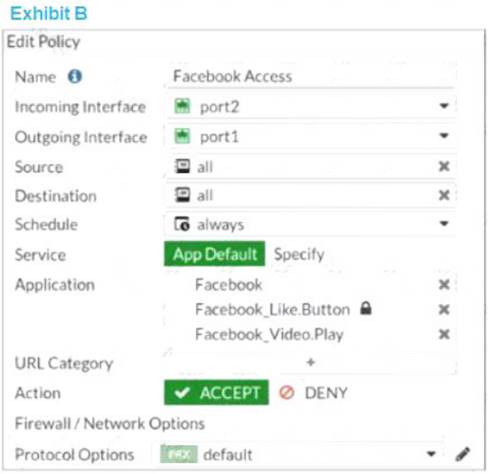
The exhibits show the SSL and authentication policy (Exhibit A) and the security policy (Exhibit B) tor Facebook.
Users are given access to the Facebook web application. They can play video content hosted on Facebook but they areunableto leavereactions on videos or other types ofposts.
Which part ofthe policy configuration must you change to resolve the issue?
- A. The SSL inspection needs tobe a deep content inspection.
- B. Force access to Facebook using the HTTP service.
- C. Additional application signatures arerequired to add to thesecurity policy.
- D. Add Facebook in the URL category in the security policy.
Answer: A
NEW QUESTION 10
Refer to the exhibit.
Which contains a session list output. Based on the information shown in the exhibit, which statement is true?
- A. Destination NAT is disabled in the firewall policy.
- B. One-to-one NAT IP pool is used in the firewall policy.
- C. Overload NAT IP pool is used in the firewall policy.
- D. Port block allocation IP pool is used in the firewall policy.
Answer: A
NEW QUESTION 11
View the exhibit.
A user behind the FortiGate is trying to go to http://www.addictinggames.com (Addicting Games). Based on this configuration, which statement is true?
- A. Addicting.Games is allowed based on the Application Overrides configuration.
- B. Addicting.Games is blocked on the Filter Overrides configuration.
- C. Addicting.Games can be allowed only if the Filter Overrides actions is set to Exempt.
- D. Addcting.Games is allowed based on the Categories configuration.
Answer: A
NEW QUESTION 12
Refer to the exhibits.

Exhibit A shows system performance output. Exhibit B shows a FortiGate configured with the default configuration of high memory usage thresholds. Based on the system performance output, which two statements are correct? (Choose two.)
- A. Administrators can access FortiGate only through the console port.
- B. FortiGate has entered conserve mode.
- C. FortiGate will start sending all files to FortiSandbox for inspection.
- D. Administrators cannot change the configuration.
Answer: CD
NEW QUESTION 13
Which of the following statements correctly describes FortiGates route lookup behavior when searching for a suitable gateway? (Choose two)
- A. Lookup is done on the first packet from the session originator
- B. Lookup is done on the last packet sent from the responder
- C. Lookup is done on every packet, regardless of direction
- D. Lookup is done on the trust reply packet from the responder
Answer: AD
NEW QUESTION 14
An administrator does not want to report the logon events of service accounts to FortiGate. What setting on the collector agent is required to achieve this?
- A. Add the support of NTLM authentication.
- B. Add useraccounts to Active Directory (AD).
- C. Add user accounts to the FortiGate group fitter.
- D. Add user accounts to the Ignore User List.
Answer: C
NEW QUESTION 15
Refer to the exhibit.
The global settings on a FortiGate device must be changed to align with company security policies. What does the Administrator account need to access the FortiGate global settings?
- A. Change password
- B. Enable restrict access to trusted hosts
- C. Change Administrator profile
- D. Enable two-factor authentication
Answer: D
NEW QUESTION 16
Examine the IPS sensor and DoS policy configuration shown in the exhibit, then answer the question below.
When detecting attacks, which anomaly, signature, or filter will FortiGate evaluate first?
- A. SMTP.Login.Brute.Force
- B. IMAP.Login.brute.Force
- C. ip_src_session
- D. Location: server Protocol: SMTP
Answer: B
NEW QUESTION 17
Refer to the exhibit.
Examine the intrusion prevention system (IPS) diagnostic command.
Which statement is correct If option 5 was used with the IPS diagnostic command and the outcome was a decrease in the CPU usage?
- A. The IPS engine was inspecting high volume of traffic.
- B. The IPS engine was unable to prevent an intrusion attack.
- C. The IPS engine was blocking all traffic.
- D. The IPS engine will continue to run in a normal state.
Answer: C
NEW QUESTION 18
Refer to the exhibit.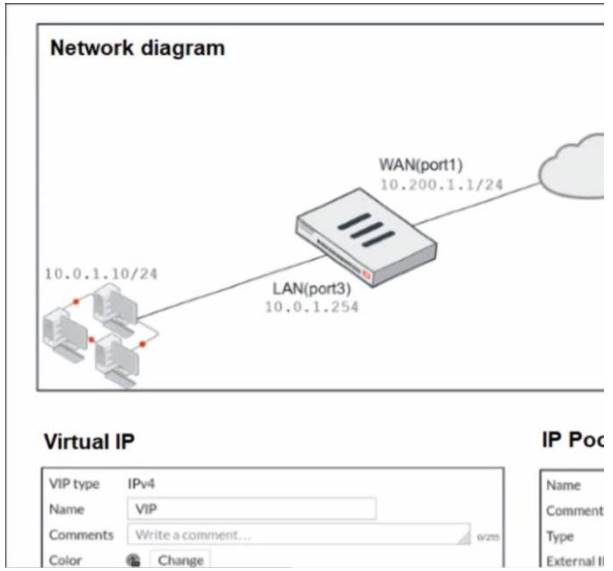
The exhibit contains a network diagram, virtual IP, IP pool, and firewall policies configuration. The WAN (port1) interface has the IP address 10.200.1.1/24.
The LAN (port3) interface has the IP address 10 .0.1.254. /24. The first firewall policy has NAT enabled using IP Pool.
The second firewall policy is configured with a VIP as the destination address.
Which IP address will be used to source NAT the internet traffic coming from a workstation with the IP address 10.0.1.10?
- A. 10.200.1.1
- B. 10.200.3.1
- C. 10.200.1.100
- D. 10.200.1.10
Answer: A
NEW QUESTION 19
......
Thanks for reading the newest NSE4_FGT-6.4 exam dumps! We recommend you to try the PREMIUM Dumps-hub.com NSE4_FGT-6.4 dumps in VCE and PDF here: https://www.dumps-hub.com/NSE4_FGT-6.4-dumps.html (163 Q&As Dumps)
