Our pass rate is high to 98.9% and the similarity percentage between our SY0-601 study guide and real exam is 90% based on our seven-year educating experience. Do you want achievements in the CompTIA SY0-601 exam in just one try? I am currently studying for the CompTIA SY0-601 exam. Latest CompTIA SY0-601 Test exam practice questions and answers, Try CompTIA SY0-601 Brain Dumps First.
Online SY0-601 free questions and answers of New Version:
NEW QUESTION 1
A security analyst is performing a forensic investigation compromised account credentials. Using the Event Viewer, the analyst able to detect the following message, ‘’Special privileges assigned to new login.’’ Several of these messages did not have a valid logon associated with the user before these privileges were assigned. Which of the following attacks is MOST likely being detected?
- A. Pass-the-hash
- B. Buffer overflow
- C. Cross-site scripting
- D. Session replay
Answer: A
NEW QUESTION 2
An organization has a growing workforce that is mostly driven by additions to the sales department. Each newly hired salesperson relies on a mobile device to conduct business. The Chief Information Officer (CIO) is wondering it the organization may need to scale down just as quickly as it scaled up. The ClO is also concerned about the organization's security and customer privacy. Which of the following would be BEST to address the ClO’s concerns?
- A. Disallow new hires from using mobile devices for six months
- B. Select four devices for the sales department to use in a CYOD model
- C. Implement BYOD for the sates department while leveraging the MDM
- D. Deploy mobile devices using the COPE methodology
Answer: C
NEW QUESTION 3
Employees are having issues accessing the company's website. Some employees report very slow performance, while others cannot the website at all. The web and security administrators search the logs and find millions of half-open connections to port 443 on the web server. Further analysis reveals thousands of different source IPs initiating this traffic. Which of the following attacks is MOST likely occurring?
- A. DDoS
- B. Man-in-the-middle
- C. MAC flooding
- D. Domain hijacking
Answer: A
NEW QUESTION 4
A development team employs a practice of bringing all the code changes from multiple team members into the same development project through automation. A tool is utilized to validate the code and track source code through version control. Which of the following BEST describes this process?
- A. Continuous delivery
- B. Continuous integration
- C. Continuous validation
- D. Continuous monitoring
Answer: B
NEW QUESTION 5
A financial organization has adopted a new secure, encrypted document-sharing application to help with its customer loan process. Some important PII needs to be shared across this new platform, but it is getting blocked by the DLP systems. Which of the following actions will BEST allow the PII to be shared with the secure application without compromising the organization’s security posture?
- A. Configure the DLP policies to allow all PII
- B. Configure the firewall to allow all ports that are used by this application
- C. Configure the antivirus software to allow the application
- D. Configure the DLP policies to whitelist this application with the specific PII
- E. Configure the application to encrypt the PII
Answer: D
NEW QUESTION 6
A security analyst is using a recently released security advisory to review historical logs, looking for the specific activity that was outlined in the advisory. Which of the following is the analyst doing?
- A. A packet capture
- B. A user behavior analysis
- C. Threat hunting
- D. Credentialed vulnerability scanning
Answer: C
NEW QUESTION 7
Which of the following control sets should a well-written BCP include? (Select THREE)
- A. Preventive
- B. Detective
- C. Deterrent
- D. Corrective
- E. Compensating
- F. Physical
- G. Recovery
Answer: ADG
NEW QUESTION 8
While checking logs, a security engineer notices a number of end users suddenly downloading files with the .t ar.gz extension. Closer examination of the files reveals they are PE32 files. The end users state they did not initiate any of the downloads. Further investigation reveals the end users all clicked on an external email containing an infected MHT file with an href link a week prior. Which of the following is MOST likely occurring?
- A. A RAT was installed and is transferring additional exploit tools.
- B. The workstations are beaconing to a command-and-control server.
- C. A logic bomb was executed and is responsible for the data transfers.
- D. A fireless virus is spreading in the local network environment.
Answer: A
NEW QUESTION 9
An organization is developing a plan in the event of a complete loss of critical systems and data. Which of the following plans is the organization MOST likely developing?
- A. Incident response
- B. Communications
- C. Disaster recovery
- D. Data retention
Answer: C
NEW QUESTION 10
A security analyst receives a SIEM alert that someone logged in to the appadmin test account, which is only used for the early detection of attacks. The security analyst then reviews the following application log: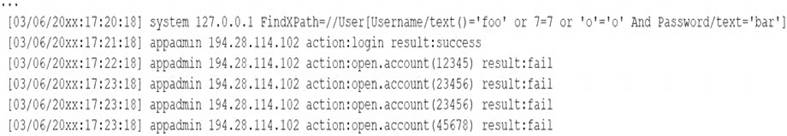
Which of the following can the security analyst conclude?
- A. A replay attack is being conducted against the application.
- B. An injection attack is being conducted against a user authentication system.
- C. A service account password may have been changed, resulting in continuous failed logins within the application.
- D. A credentialed vulnerability scanner attack is testing several CVEs against the application.
Answer: C
NEW QUESTION 11
A consultant is configuring a vulnerability scanner for a large, global organization in multiple countries. The consultant will be using a service account to scan systems with administrative privileges on a weekly basis, but there is a concern that hackers could gain access to account to the account and pivot through the global network. Which of the following would be BEST to help mitigate this concern?
- A. Create consultant accounts for each region, each configured with push MFA notifications.
- B. Create one global administrator account and enforce Kerberos authentication
- C. Create different accounts for each regio
- D. limit their logon times, and alert on risky logins
- E. Create a guest account for each regio
- F. remember the last ten passwords, and block password reuse
Answer: C
NEW QUESTION 12
A cybersecurity administrator has a reduced team and needs to operate an on-premises network and security infrastructure efficiently. To help with the situation, the administrator decides to hire a service provider. Which of the following should the administrator use?
- A. SDP
- B. AAA
- C. IaaS
- D. MSSP
- E. Microservices
Answer: D
NEW QUESTION 13
A workwide manufacturing company has been experiencing email account compromised. In one incident, a user logged in from the corporate office in France, but then seconds later, the same user account attempted a login from Brazil. Which of the following account policies would BEST prevent this type of attack?
- A. Network location
- B. Impossible travel time
- C. Geolocation
- D. Geofencing
Answer: D
NEW QUESTION 14
A security analyst is preparing a threat for an upcoming internal penetration test. The analyst needs to identify a method for determining the tactics, techniques, and procedures of a threat against the organization’s network. Which of the following will the analyst MOST likely use to accomplish the objective?
- A. A table exercise
- B. NST CSF
- C. MTRE ATT$CK
- D. OWASP
Answer: A
NEW QUESTION 15
A symmetric encryption algorithm Is BEST suited for:
- A. key-exchange scalability.
- B. protecting large amounts of data.
- C. providing hashing capabilities,
- D. implementing non-repudiation.
Answer: D
NEW QUESTION 16
Which of the following BEST explains the reason why a server administrator would place a document named password.txt on the desktop of an administrator account on a server?
- A. The document is a honeyfile and is meant to attract the attention of a cyberintruder.
- B. The document is a backup file if the system needs to be recovered.
- C. The document is a standard file that the OS needs to verify the login credentials.
- D. The document is a keylogger that stores all keystrokes should the account be compromised.
Answer: A
NEW QUESTION 17
An organization has hired a security analyst to perform a penetration test. The analyst captures 1Gb worth of inbound network traffic to the server and transfer the pcap back to the machine for analysis. Which of the following tools should the analyst use to further review the pcap?
- A. Nmap
- B. cURL
- C. Netcat
- D. Wireshark
Answer: D
NEW QUESTION 18
A technician needs to prevent data loss in a laboratory. The laboratory is not connected to any external networks. Which of the following methods would BEST prevent data? (Select TWO)
- A. VPN
- B. Drive encryption
- C. Network firewall
- D. File-level encryption
- E. USB blocker
- F. MFA
Answer: BE
NEW QUESTION 19
A company is launching a new internet platform for its clients. The company does not want to implement its own authorization solution but instead wants to rely on the authorization provided by another platform. Which of the following is the BEST approach to implement the desired solution?
- A. OAuth
- B. TACACS+
- C. SAML
- D. RADIUS
Answer: D
NEW QUESTION 20
The following is an administrative control that would be MOST effective to reduce the occurrence of malware execution?
- A. Security awareness training
- B. Frequency of NIDS updates
- C. Change control procedures
- D. EDR reporting cycle
Answer: A
NEW QUESTION 21
A root cause analysis reveals that a web application outage was caused by one of the company’s developers uploading a newer version of the third-party libraries that were shared among several applications. Which of the following implementations would be BEST to prevent the issue from reoccurring?
- A. CASB
- B. SWG
- C. Containerization
- D. Automated failover
Answer: C
NEW QUESTION 22
A company recently added a DR site and is redesigning the network. Users at the DR site are having issues browsing websites. INSTRUCTIONS
Click on each firewall to do the following:  Deny cleartext web traffic.
Deny cleartext web traffic. Ensure secure management protocols are used.
Ensure secure management protocols are used.  Resolve issues at the DR site.
Resolve issues at the DR site.
The ruleset order cannot be modified due to outside constraints.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.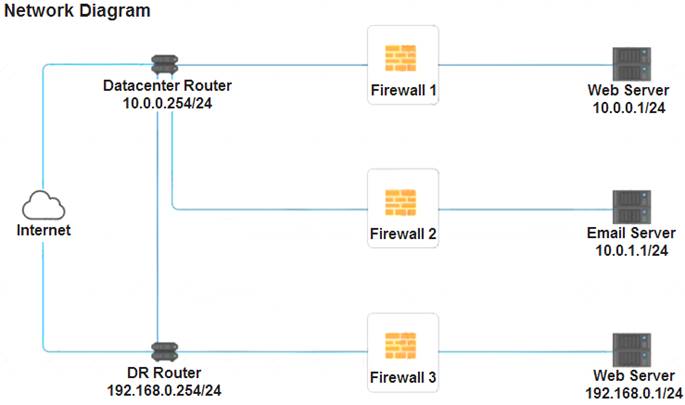
- A.
Answer: A
Explanation:
See explanation below.
Explanation
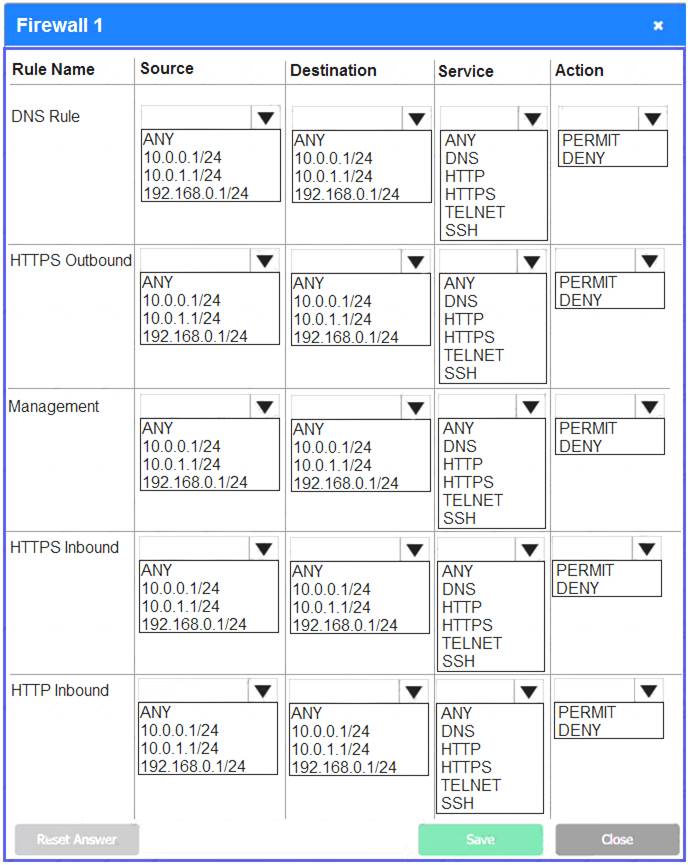
Firewall 1: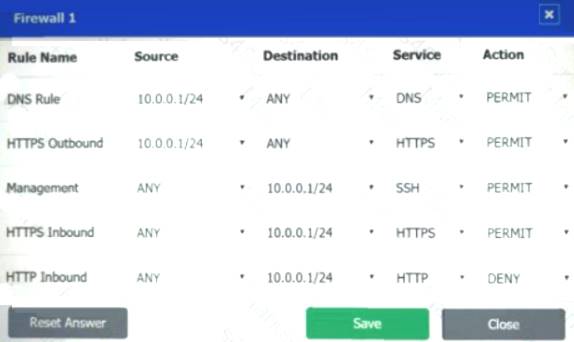
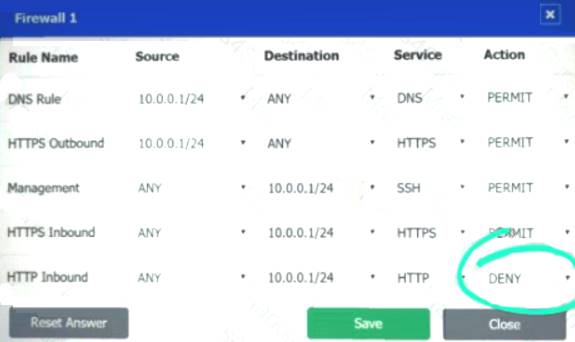
DNS Rule – ANY --> ANY --> DNS --> PERMIT
HTTPS Outbound – 10.0.0.1/24 --> ANY --> HTTPS --> PERMIT Management – ANY --> ANY --> SSH --> PERMIT
HTTPS Inbound – ANY --> ANY --> HTTPS --> PERMIT HTTP Inbound – ANY --> ANY --> HTTP --> DENY
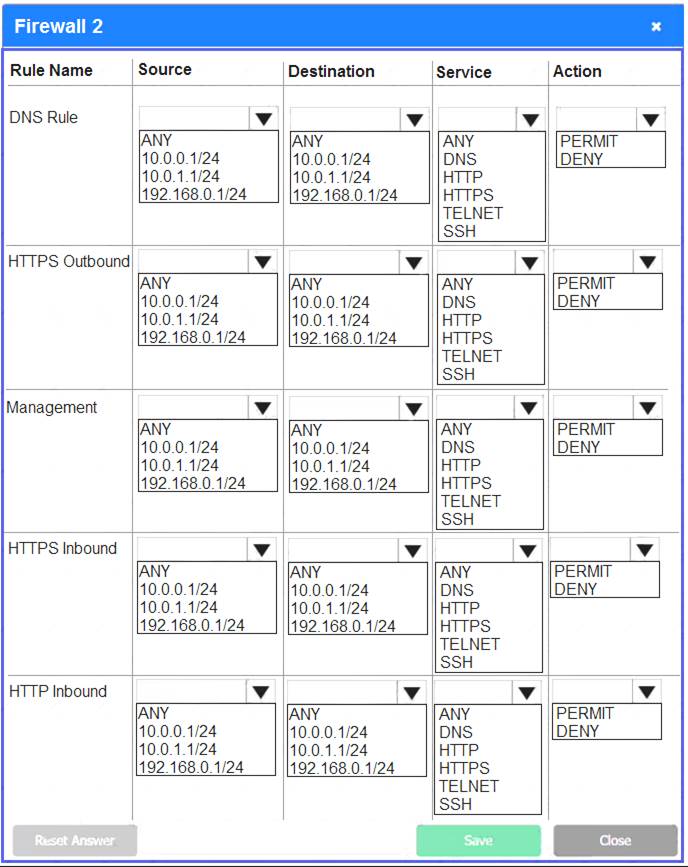
Firewall 2: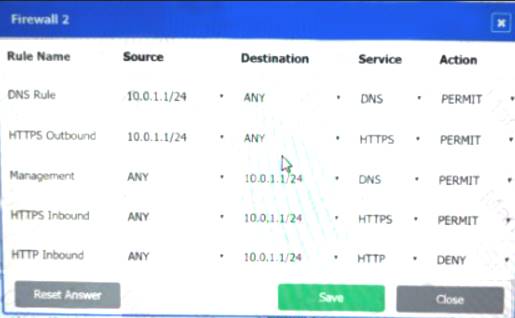
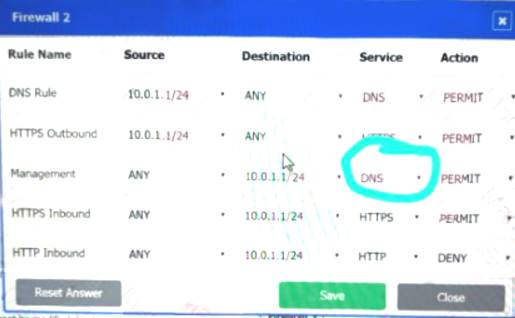
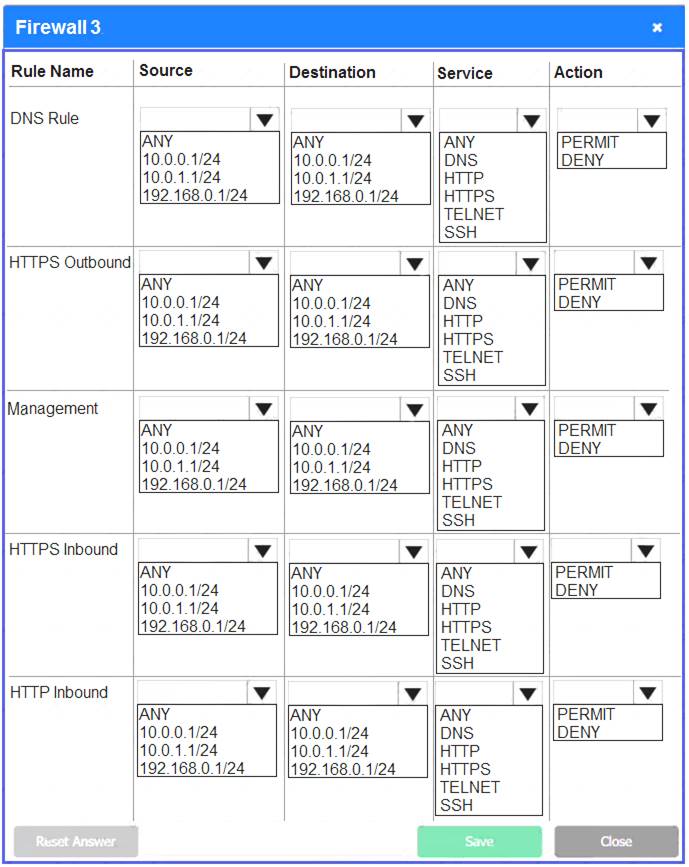
Firewall 3: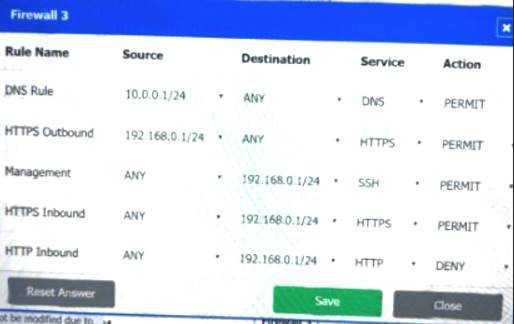
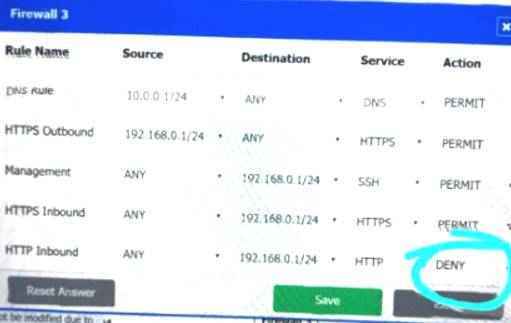
DNS Rule – ANY --> ANY --> DNS --> PERMIT
HTTPS Outbound – 192.168.0.1/24 --> ANY --> HTTPS --> PERMIT Management – ANY --> ANY --> SSH --> PERMIT
HTTPS Inbound – ANY --> ANY --> HTTPS --> PERMIT HTTP Inbound – ANY --> ANY --> HTTP --> DENY
NEW QUESTION 23
An employee has been charged with fraud and is suspected of using corporate assets. As authorities collect evidence, and to preserve the admissibility of the evidence, which of the following forensic techniques should be used?
- A. Order of volatility
- B. Data recovery
- C. Chain of custody
- D. Non-repudiation
Answer: C
NEW QUESTION 24
......
P.S. Easily pass SY0-601 Exam with 218 Q&As Dumps-files.com Dumps & pdf Version, Welcome to Download the Newest Dumps-files.com SY0-601 Dumps: https://www.dumps-files.com/files/SY0-601/ (218 New Questions)
