we provide Validated CompTIA SY0-601 test question which are the best for clearing SY0-601 test, and to get certified by CompTIA CompTIA Security+ Exam. The SY0-601 Questions & Answers covers all the knowledge points of the real SY0-601 exam. Crack your CompTIA SY0-601 Exam with latest dumps, guaranteed!
CompTIA SY0-601 Free Dumps Questions Online, Read and Test Now.
NEW QUESTION 1
A new security engineer has started hardening systems. One of the hardening techniques the engineer is using involves disabling remote logins to the NAS. Users are now reporting the inability to use SCP to transfer files to the NAS, even through the data is still viewable from the user’s PCs. Which of the following is the most likely cause of this issue?
- A. TFTP was disabled on the local hosts
- B. SSH was turned off instead of modifying the configuration file
- C. Remote login was disabled in the networkd.config instead of using the sshd.conf
- D. Network services are no longer running on the NAS
Answer: B
Explanation:
SSH stands for Secure Shell Protocol, which is a cryptographic network protocol that allows secure remote login and command execution on a network device12. SSH can encrypt both the authentication information and the data being exchanged between the client and the server2. SSH can be used to access and manage a NAS device remotely3.
NEW QUESTION 2
A security analyst receives an alert from the company's S1EM that anomalous activity is coming from a local source IP address of 192 168 34.26 The Chief Information Security Officer asks the analyst to block the originating source Several days later another employee opens an internal ticket stating that vulnerability scans are no longer being performed property. The IP address the employee provides is 192 168.34 26. Which of the following describes this type of alert?
- A. True positive
- B. True negative
- C. False positive
- D. False negative
Answer: C
Explanation:
A false positive is a type of alert that indicates a security incident when there is none. It can be caused by misconfigured or overly sensitive security tools or systems that generate false or irrelevant alerts. In this case, the alert from the company’s SIEM that Mimikatz attempted to run on the remote systems was a false positive because it was triggered by a legitimate vulnerability scanning tool that uses Mimikatz as part of its functionality.
NEW QUESTION 3
A security analyst is investigating a malware incident at a company The malware is accessing a
command-and-control website at www.comptia.com. All outbound internet traffic is logged to a syslog server and stored in /logfiles/messages Which of the following commands would be best for the analyst to use on the syslog server to search for recent traffic to the command-and-control website?
- A. head -500 ww
- B. compt ia.com | grep /logfiles/messages
- C. cat /logfiles/messages I tail -500 www.comptia.com
- D. tail -500 /logfiles/messages I grep www.cornptia.com
- E. grep -500 /logfiles/messages I cat www.comptia.cctn
Answer: C
Explanation:
tail is a Linux command that can be used to display the last part of a file. grep is a Linux command that can be used to search for a pattern in a file or input. The pipe symbol (|) is used to connect two commands and pass the output of one command as the input of another command. The best command for the analyst to use on the syslog server to search for recent traffic to the command-and-control website is tail -500 /logfiles/messages | grep www.comptia.com. This command would display the last 500 lines of the /logfiles/messages file and filter them by the pattern www.comptia.com, which is the domain name of the command-and-control website.
This way, the analyst can see any syslog messages that contain the domain name of the malicious website and investigate them further. 2122 [23] References: CompTIA Security+ SY0-601 Certification Study Guide Chapter 11: Explaining Digital Forensics Concepts, page 498; tail (Unix) - Wikipedia; grep - Wikipedia; [Ho To Use grep Command In Linux / UNIX - nixCraft]
NEW QUESTION 4
An account was disabled atter several failed and successful login connections were made from various parts of the Word at various times. A security analysts investigating the issue. Which of the following account policies most likely triggered the action to disable the
- A. Time based logins
- B. Password history
- C. Geofencing
- D. Impossible travel time
Answer: D
Explanation:
Impossible travel time is a policy that detects and blocks login attempts from locations that are geographically impossible to reach from the previous login location within a certain time frame. For example, if a user logs in from New York and then tries to log in from Tokyo within an hour, the policy would flag this as impossible travel time and disable the account. This policy helps prevent unauthorized access from compromised credentials or attackers using proxy servers. References: 1
CompTIA Security+ Certification Exam Objectives
page 6, Domain 1.0: Attacks, Threats, and Vulnerabilities, Objective 1.2: Compare and contrast different types of social engineering techniques 2
CompTIA Security+ Certification Exam Objectives, page 14, Domain 3.0:
Implementation, Objective 3.4: Implement identity and account management controls 3
https://docs.microsoft.com/en-us/azure/active-directory/identity-protection/howto-sign-in-risk-policy#impossi
NEW QUESTION 5
Which of the following are the MOST likely vectors for the unauthorized inclusion of vulnerable code in a software company’s final software releases? (Select TWO.)
- A. Unsecure protocols
- B. Use of penetration-testing utilities
- C. Weak passwords
- D. Included third-party libraries
- E. Vendors/supply chain
- F. Outdated anti-malware software
Answer: DE
Explanation:
The most likely vectors for the unauthorized inclusion of vulnerable code in a software company's final software releases are included third-party libraries and vendors/supply chain. References: CompTIA Security+ Study Guide by Emmett Dulaney, Chapter 8: Application, Data, and Host Security, Supply Chain and Software Development Life Cycle
NEW QUESTION 6
A security analyst needs an overview of vulnerabilities for a host on the network. Which of the following is the BEST type of scan for the analyst to run to discover which vulnerable services are running?
- A. Non-credentialed
- B. Web application
- C. Privileged
- D. Internal
Answer: C
Explanation:
Privileged scanning, also known as credentialed scanning, is a type of vulnerability scanning that uses a valid user account to log in to the target host and examine vulnerabilities from a trusted user’s perspective. It can provide more accurate and comprehensive results than unprivileged scanning, which does not use any credentials and only scans for externally visible vulnerabilities.
NEW QUESTION 7
A security manager needs to assess the security posture of one of the organization's vendors. The contract with the vendor does not allow for auditing of the vendor's security controls. Which of (he following should the manager request to complete the assessment?
- A. A service-level agreement
- B. A business partnership agreement
- C. A SOC 2 Type 2 report
- D. A memorandum of understanding
Answer: C
Explanation:
SOC 2 (Service Organization Control 2) is a type of audit report that evaluates the controls of service providers to verify their compliance with industry standards for security, availability, processing integrity,
confidentiality, and privacy. A Type 2 report is based on an audit that tests the effectiveness of the controls over a period of time, unlike a Type 1 report which only evaluates the design of the controls at a specific point in time.
A SOC 2 Type 2 report would provide evidence of the vendor's security controls and how effective they are over time, which can help the security manager assess the vendor's security posture despite the vendor not allowing for a direct audit.
The security manager should request a SOC 2 Type 2 report to assess the security posture of the vendor. References: CompTIA Security+ Study Guide: Exam SY0-601, Chapter 5
NEW QUESTION 8
The concept of connecting a user account across the systems of multiple enterprises is best known as:
- A. federation
- B. a remote access policy.
- C. multifactor authentication
- D. single sign-on.
Answer: D
Explanation:
The concept of connecting a user account across the systems of multiple enterprises is best known as federation. Federation is a process that allows users to authenticate once and access multiple resources or services across different domains or organizations. For example, a user can use their Google account to sign in to various websites or applications that support federation, without creating separate accounts or passwords for each one. Federation can improve user convenience and security, as well as reduce administrative overhead.
NEW QUESTION 9
Which of the following is a reason why a forensic specialist would create a plan to preserve data after an
incident and prioritize the sequence for performing forensic analysis?
- A. Order of volatility
- B. Preservation of event logs
- C. Chain of custody
- D. Compliance with legal hold
Answer: A
Explanation:
Order of volatility is the order in which a forensic specialist should collect evidence based on how quickly the data can be lost or altered. The most volatile data, such as CPU registers and cache, should be collected first, followed by less volatile data, such as disk drives and archival media. Order of volatility helps preserve the integrity and validity of the evidence and prevent data loss or corruption123 References: CompTIA Security SY0-601 Certification Study Guide, Chapter 11: Explaining Digital Forensics Concepts, page 494; Order of Volatility - Computer Forensics Recruiter; Order of Volatility – CompTIA Security+ SY0-401: 2.4; CFR an Order of Volatility - Get Certified Get Ahead
NEW QUESTION 10
Which of the following BEST describes the team that acts as a referee during a penetration-testing exercise?
- A. White team
- B. Purple team
- C. Green team
- D. Blue team
- E. Red team
Answer: A
Explanation:
During a penetration testing exercise, the white team is responsible for acting as a referee and providing oversight and support to ensure that the testing is conducted safely and effectively. They may also be responsible for determining the rules and guidelines of the exercise, monitoring the progress of the teams, and providing feedback and insights on the strengths and weaknesses of the organization's security measures.
NEW QUESTION 11
Multiple beaconing activities to a malicious domain have been observed. The malicious domain is hosting malware from various endpoints on the network. Which of the following technologies would be best to correlate the activities between the different endpoints?
- A. Firewall
- B. SIEM
- C. IPS
- D. Protocol analyzer
Answer: B
Explanation:
SIEM stands for Security Information and Event Management, which is a technology that collects, analyzes, and correlates data from multiple sources, such as firewall logs, IDS/IPS alerts, network devices, applications, and endpoints. SIEM provides real-time monitoring and alerting of security events, as well as historical analysis and reporting for compliance and forensic purposes.
A SIEM technology would be best to correlate the activities between the different endpoints that are beaconing to a malicious domain. A SIEM can detect the malicious domain by comparing it with threat intelligence feeds or known indicators of compromise (IOCs). A SIEM can also identify the endpoints that are communicating with the malicious domain by analyzing the firewall logs and other network traffic data. A SIEM can alert the security team of the potential compromise and provide them with relevant information for investigation and remediation.
NEW QUESTION 12
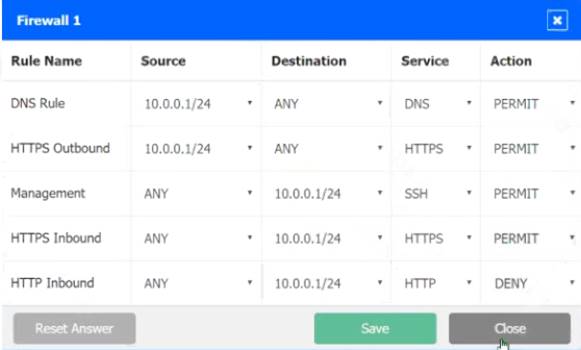
A company recently added a DR site and is redesigning the network. Users at the DR site are having issues browsing websites.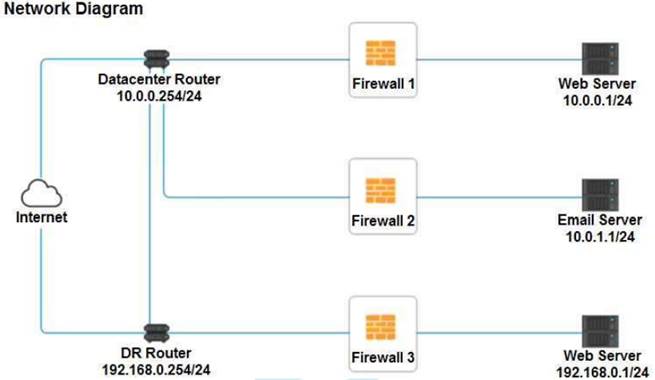
INSTRUCTIONS
Click on each firewall to do the following:
* 1. Deny cleartext web traffic
* 2. Ensure secure management protocols are used.
* 3. Resolve issues at the DR site.
The ruleset order cannot be modified due to outside constraints.
Hat any time you would like to bring back the initial state of the simulation, please dick the Reset All button.
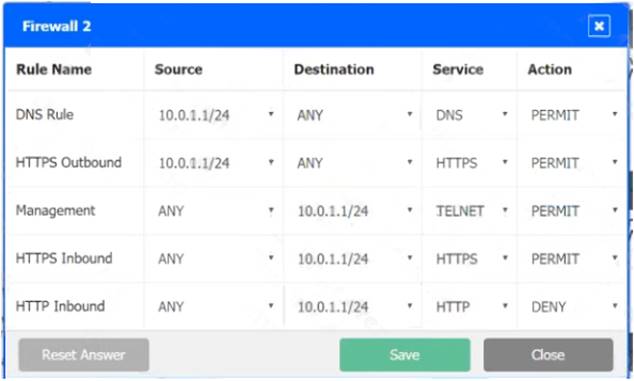
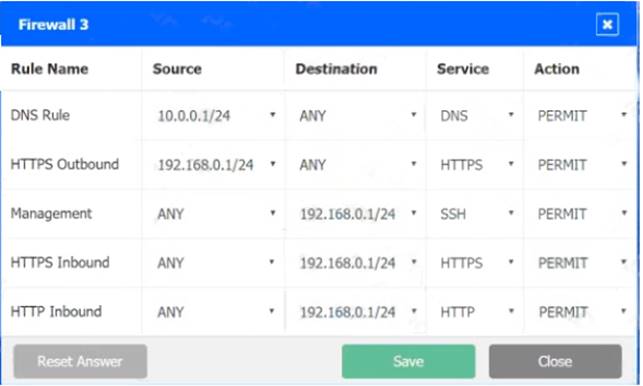
Solution:
In Firewall 1, HTTP inbound Action should be DENY. As shown below
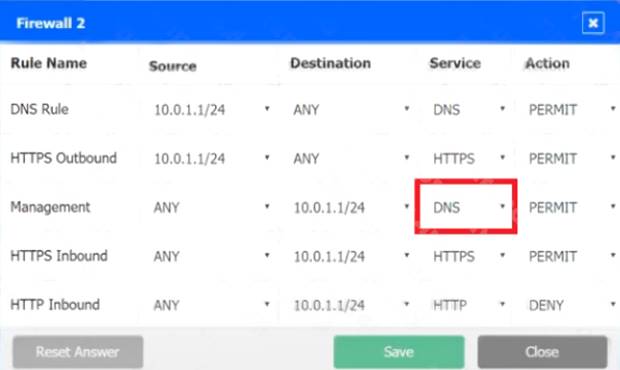
In Firewall 2, Management Service should be DNS, As shown below.
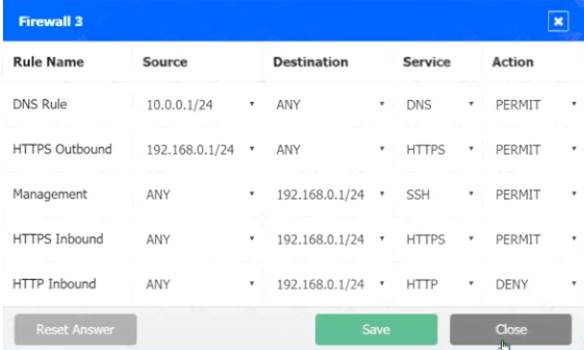
In Firewall 3, HTTP Inbound Action should be DENY, as shown below
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 13
A company uses specially configured workstations for any work that requires administrator privileges to its Tier 0 and Tier 1 systems The company follows a strict process to harden systems immediately upon delivery Even with these strict security measures in place an incident occurred from one of the workstations The root cause appears to be that the SoC was tampered with or replaced Which of the following most likely occurred?
- A. Fileless malware
- B. A downgrade attack
- C. A supply-chain attack
- D. A logic bomb
- E. Misconfigured BIOS
Answer: C
Explanation:
A supply-chain attack is a type of cyberattack that targets a trusted third-party vendor who offers services or products vital to the supply chain. A supply-chain attack can occur in software or hardware. In this case, the most likely scenario is that the SoC (system on chip) was compromised by a malicious actor before it was delivered to the company, either by tampering with or replacing it with a malicious version. This would allow the attacker to gain access to the company’s systems through the specially configured workstations
NEW QUESTION 14
Which of the following would MOST likely be identified by a credentialed scan but would be missed by an uncredentialed scan?
- A. Vulnerabilities with a CVSS score greater than 6.9.
- B. Critical infrastructure vulnerabilities on non-IP protocols.
- C. CVEs related to non-Microsoft systems such as printers and switches.
- D. Missing patches for third-party software on Windows workstations and servers.
Answer: D
Explanation:
An uncredentialed scan would miss missing patches for third-party software on Windows workstations and servers. A credentialed scan, however, can scan the registry and file system to determine the patch level of third-party applications. References: CompTIA Security+ Study Guide by Emmett Dulaney, Chapter 4: Identity and Access Management, The Importance of Credentialing Scans
NEW QUESTION 15
Cloud security engineers are planning to allow and deny access to specific features in order to in-crease data security. Which of the following cloud features is the most appropriate to ensure ac-cess is granted properly?
- A. API integrations
- B. Auditing
- C. Resource policies
- D. Virtual networks
Answer: C
Explanation:
Resource policies are cloud features that allow and deny access to specific features in order to increase data security. Resource policies are rules or statements that define what actions can be performed on a particular resource by which entities under what conditions. Resource policies can be attached to cloud resources such as virtual machines, storage accounts, databases, or functions. Resource policies can help enforce security best practices, compliance requirements, and cost management. Resource policies can also help implement the principle of least privilege, which grants users only the minimum level of access they need to perform their tasks.
NEW QUESTION 16
An organization needs to implement more stringent controls over administrator/root credentials and service accounts. Requirements for the project include:
* Check-in/checkout of credentials
* The ability to use but not know the password
* Automated password changes
* Logging of access to credentials
Which of the following solutions would meet the requirements?
- A. OAuth 2.0
- B. Secure Enclave
- C. A privileged access management system
- D. An OpenID Connect authentication system
Answer: C
Explanation:
A privileged access management (PAM) system is a solution that helps protect organizations against cyberthreats by monitoring, detecting, and preventing unauthorized privileged access to critical resources12. A PAM system can meet the requirements of the project by providing features such as: Check-in/checkout of credentials: A PAM system can store and manage privileged credentials in a secure vault, and allow authorized users to check out credentials when needed and check them back in when done. This reduces the risk of credential theft, misuse, or sharin2g3.
Check-in/checkout of credentials: A PAM system can store and manage privileged credentials in a secure vault, and allow authorized users to check out credentials when needed and check them back in when done. This reduces the risk of credential theft, misuse, or sharin2g3. The ability to use but not know the password: A PAM system can enable users to access privileged accounts or resources without revealing the actual password, using methods such as password injection, session proxy, or single sign-on23. This prevents users from copying, changing, or sharing password2s.
The ability to use but not know the password: A PAM system can enable users to access privileged accounts or resources without revealing the actual password, using methods such as password injection, session proxy, or single sign-on23. This prevents users from copying, changing, or sharing password2s. Automated password changes: A PAM system can automatically rotate and update passwords for privileged accounts according to predefined policies, such as frequency, complexity, and uniqueness23
Automated password changes: A PAM system can automatically rotate and update passwords for privileged accounts according to predefined policies, such as frequency, complexity, and uniqueness23
. This ensures that passwords are always strong and unpredictable, and reduces the risk of password
reuse or compromise2. Logging of access to credentials: A PAM system can record and audit all activities related to privileged access, such as who accessed what credentials, when, why, and what they did with them23. This provides visibility and accountability for privileged access, and enables detection and investigation of anomalies or incidents2.
Logging of access to credentials: A PAM system can record and audit all activities related to privileged access, such as who accessed what credentials, when, why, and what they did with them23. This provides visibility and accountability for privileged access, and enables detection and investigation of anomalies or incidents2.
A PAM system is different from OAuth 2.0, which is an authorization framework that enables third-party applications to obtain limited access to an HTTP service on behalf of a resource owner4. OAuth 2.0 does not provide the same level of control and security over privileged access as a PAM system does.
A PAM system is also different from a secure enclave, which is a hardware-based security feature that creates an isolated execution environment within a processor to protect sensitive data from unauthorized access or modification5. A secure enclave does not provide the same functionality as a PAM system for managing privileged credentials and access.
A PAM system is also different from an OpenID Connect authentication system, which is an identity layer on top of OAuth 2.0 that enables users to verify their identity across multiple websites using a single login6. OpenID Connect does not provide the same scope and granularity as a PAM system for controlling and monitoring privileged access.
NEW QUESTION 17
A Chief Information Security Officer (CISO) is evaluating the dangers involved in deploying a new ERP system for the company. The CISO categorizes the system, selects the controls that apply to the system, implements the controls, and then assesses the success of the controls before authorizing the system. Which of the following is the CISO using to evaluate the environment for this new ERP system?
- A. The Diamond Model of Intrusion Analysis
- B. CIS Critical Security Controls
- C. NIST Risk Management Framework
- D. ISO 27002
Answer: C
Explanation:
The NIST Risk Management Framework (RMF) is a process for evaluating the security of a system and implementing controls to reduce potential risks associated with it. The RMF process involves categorizing the system, selecting the controls that apply to the system, implementing the controls, and then assessing the success of the controls before authorizing the system. For more information on the NIST Risk Management Framework and other security processes, refer to the CompTIA Security+ SY0-601 Official Text Book and Resources.
NEW QUESTION 18
A security incident has been resolved Which of the following BEST describes the importance of the final phase of the incident response plan?
- A. It examines and documents how well the team responded discovers what caused the incident, and determines how the incident can be avoided in the future
- B. It returns the affected systems back into production once systems have been fully patched, data restored and vulnerabilities addressed
- C. It identifies the incident and the scope of the breach how it affects the production environment, and the ingress point
- D. It contains the affected systems and disconnects them from the network, preventing further spread of the attack or breach
Answer: A
Explanation:
The final phase of an incident response plan is the post-incident activity, which involves examining and documenting how well the team responded, discovering what caused the incident, and determining how the incident can be avoided in the future. References: CompTIA Security+ Certification Exam Objectives - 2.5 Given a scenario, analyze potential indicators to determine the type of attack. Study Guide: Chapter 5, page 225.
NEW QUESTION 19
......
P.S. Easily pass SY0-601 Exam with 534 Q&As Dumps-files.com Dumps & pdf Version, Welcome to Download the Newest Dumps-files.com SY0-601 Dumps: https://www.dumps-files.com/files/SY0-601/ (534 New Questions)
