Act now and download your CompTIA SY0-601 test today! Do not waste time for the worthless CompTIA SY0-601 tutorials. Download Down to date CompTIA CompTIA Security+ Exam exam with real questions and answers and begin to learn CompTIA SY0-601 with a classic professional.
Free demo questions for CompTIA SY0-601 Exam Dumps Below:
NEW QUESTION 1
To reduce and limit software and infrastructure costs the Chief Information Officer has requested to move
email services to the cloud. The cloud provider and the organization must have secunty controls to protect sensitive data Which of the following cloud services would best accommodate the request?
- A. laaS
- B. PaaS
- C. DaaS
- D. SaaS
Answer: D
Explanation:
SaaS (Software as a Service) is a cloud model that provides clients with applications and software that are hosted and managed by a cloud provider over the internet. It can move email services to the cloud by allowing clients to access and use email applications without installing or maintaining them on their own devices or servers
NEW QUESTION 2
Which of the following components can be used to consolidate and forward inbound internet traffic to multiple cloud environments though a single firewall?
- A. Transit gateway
- B. Cloud hot site
- C. Edge computing
- D. DNS sinkhole
Answer: A
Explanation:
A transit gateway is a network transit hub that can be used to interconnect virtual private clouds (VPCs) and on-premises networks. A transit gateway can consolidate and forward inbound internet traffic to multiple cloud environments through a single firewall by offering the following features: Attachments that can connect one or more VPCs, a Connect SD-WAN/third-party network appliance, an AWS Direct Connect gateway, a peering connection with another transit gateway, or a VPN connection to a transit gateway.
Attachments that can connect one or more VPCs, a Connect SD-WAN/third-party network appliance, an AWS Direct Connect gateway, a peering connection with another transit gateway, or a VPN connection to a transit gateway. Transit gateway route table that can include dynamic and static routes that decide the next hop based on the destination IP address of the packet.
Transit gateway route table that can include dynamic and static routes that decide the next hop based on the destination IP address of the packet. Associations and route propagation that can link each attachment with a route table and dynamically
Associations and route propagation that can link each attachment with a route table and dynamically
propagate routes to or from a transit gateway route table. References: What is a transit gateway? - Amazon VPC; Network Gateway – AWS Transit Gateway – Amazon Web Services; Configure VPN gateway transit for virtual network peering; AWS — Difference between VPC Peering and Transit Gateway
NEW QUESTION 3
An organization's Chief Information Security Officer is creating a position that will be responsible for implementing technical controls to protect data, including ensuring backups are properly maintained Which of the following roles would MOST likely include these responsibilities?
- A. Data protection officer
- B. Data owner
- C. Backup administrator
- D. Data custodian
- E. Internal auditor
Answer: C
Explanation:
The role that would most likely include the responsibilities of implementing technical controls to protect data and ensuring backups are properly maintained would be a Backup Administrator. A Backup Administrator is responsible for maintaining and managing an organization's backup systems and procedures, which includes ensuring that backups are properly configured, tested and securely stored. They are also responsible for the recovery of data in case of a disaster or data loss.
NEW QUESTION 4
Which of the following is the MOST secure but LEAST expensive data destruction method for data that is stored on hard drives?
- A. Pulverizing
- B. Shredding
- C. Incinerating
- D. Degaussing
Answer: B
Explanation:
Shredding may be the most secure and cost-effective way to destroy electronic data in any media that contain hard drives or solid-state drives and have reached their end-of-life1. Shredding reduces electronic devices to pieces no larger than 2 millimeters2. Therefore, shredding is the most secure but least expensive data destruction method for data that is stored on hard drives.
NEW QUESTION 5
A user enters a password to log in to a workstation and is then prompted to enter an authentication code Which of the following MFA factors or attributes are being utilized in the authentication process? {Select two).
- A. Something you know
- B. Something you have
- C. Somewhere you are
- D. Someone you know
- E. Something you are
- F. Something you can do
Answer: AB
Explanation:
MFA (Multi-Factor Authentication) is a method of verifying a user’s identity by requiring two or more factors or attributes that belong to different categories. The categories are something you know (such as a password or a PIN), something you have (such as a token or a smart card), something you are (such as a fingerprint or an iris scan), something you do (such as a gesture or a voice command), and somewhere you are (such as a location or an IP address). In this case, the user enters a password (something you know) and then receives an authentication code (something you have) to log in to a workstation.
NEW QUESTION 6
A security administrator Is managing administrative access to sensitive systems with the following requirements:
• Common login accounts must not be used (or administrative duties.
• Administrative accounts must be temporal in nature.
• Each administrative account must be assigned to one specific user.
• Accounts must have complex passwords.
• Audit trails and logging must be enabled on all systems.
Which of the following solutions should the administrator deploy to meet these requirements?
- A. ABAC
- B. SAML
- C. PAM
- D. CASB
Answer: C
Explanation:
The best solution to meet the given requirements is to deploy a Privileged Access Management (PAM) solution. PAM solutions allow administrators to create and manage administrative accounts that are assigned to specific users and that have complex passwords. Additionally, PAM solutions provide the ability to enable audit trails and logging on all systems, as well as to set up temporal access for administrative accounts. SAML, ABAC, and CASB are not suitable for this purpose.
NEW QUESTION 7
Which of the following uses six initial steps that provide basic control over system security by including hardware and software inventory, vulnerability management, and continuous monitoring to minimize risk in all network environments?
- A. ISO 27701
- B. The Center for Internet Security
- C. SSAE SOC 2
- D. NIST Risk Management Framework
Answer: B
Explanation:
The Center for Internet Security (CIS) uses six initial steps that provide basic control over system security, including hardware and software inventory, vulnerability management, and continuous monitoring to minimize risk in all network environments. References: CompTIA Security+ Certification Exam Objectives 1.1: Compare and contrast different types of security concepts.
CompTIA Security+ Certification Exam Objectives 1.1: Compare and contrast different types of security concepts. CompTIA Security+ Study Guide, Sixth Edition, pages 15-16
CompTIA Security+ Study Guide, Sixth Edition, pages 15-16
NEW QUESTION 8
A systems administrator set up an automated process that checks for vulnerabilities across the entire
environment every morning. Which of the following activities is the systems administrator conducting?
- A. Scanning
- B. Alerting
- C. Reporting
- D. Archiving
Answer: A
Explanation:
Scanning is the activity of checking for vulnerabilities across the network, systems, or applications. It can be done manually or automatically using tools such as vulnerability scanners, port scanners, or network mappers. Scanning can help identify and remediate potential security issues before they are exploited.
NEW QUESTION 9
An information security manager for an organization is completing a PCI DSS self-assessment for the first time. which of the is following MOST likely reason for this type of assessment?
- A. An international expansion project is currently underway.
- B. Outside consultants utilize this tool to measure security maturity.
- C. The organization is expecting to process credit card information.
- D. A government regulator has requested this audit to be completed
Answer: C
Explanation:
PCI DSS (Payment Card Industry Data Security Standard) is a set of security standards designed to ensure that all companies that accept, process, store, or transmit credit card information maintain a secure environment. Any organization that accepts credit card payments is required to comply with PCI DSS.
NEW QUESTION 10
A user is trying to upload a tax document, which the corporate finance department requested, but a security program IS prohibiting the upload A security analyst determines the file contains Pll, Which of
the following steps can the analyst take to correct this issue?
- A. Create a URL filter with an exception for the destination website.
- B. Add a firewall rule to the outbound proxy to allow file uploads
- C. Issue a new device certificate to the user's workstation.
- D. Modify the exception list on the DLP to allow the upload
Answer: D
Explanation:
Data Loss Prevention (DLP) policies are used to identify and protect sensitive data, and often include a list of exceptions that allow certain types of data to be uploaded or shared. By modifying the exception list on the DLP, the security analyst can allow the tax document to be uploaded without compromising the security of the system. (Reference: CompTIA Security+ SY0-601 Official Textbook, page 479-480)
NEW QUESTION 11
Which of the following has been implemented when a host-based firewall on a legacy Linux system allows connections from only specific internal IP addresses?
- A. Compensating control
- B. Network segmentation
- C. Transfer of risk
- D. SNMP traps
Answer: A
Explanation:
A compensating control is a type of security control that is implemented in lieu of a recommended security measure that is deemed too difficult or impractical to implement at the present time. A compensating control must provide equivalent or comparable protection for the system or network and meet the intent and rigor of the original security requirement. An example of a compensating control is using a host-based firewall on a legacy Linux system to allow connections from only specific internal IP addresses, as it can provide a similar level of defense as a network firewall that may not be compatible with the system. References: https://www.techtarget.com/whatis/definition/compensating-control
https://www.techtarget.com/whatis/definition/compensating-control https://reciprocity.com/resources/whats-the-difference-between-compensating-controls-and-mitigating-co
https://reciprocity.com/resources/whats-the-difference-between-compensating-controls-and-mitigating-co
NEW QUESTION 12
A security architect is required to deploy to conference rooms some workstations that will allow sensitive data to be displayed on large screens. Due to the nature of the data, it cannot be stored in the conference rooms. The file share is located in a local data center. Which of the following should the security architect recommend to best meet the requirement?
- A. Fog computing and KVMs
- B. VDI and thin clients
- C. Private cloud and DLP
- D. Full drive encryption and thick clients
Answer: B
Explanation:
VDI and thin clients are the best solution to deploy to conference rooms for displaying sensitive data on large screens. VDI stands for virtual desktop infrastructure, which is a technology that hosts the desktop operating systems and applications on a central server or cloud and allows users to access them remotely. Thin clients are devices that have minimal hardware and software components and rely on a network connection to the VDI system. By using VDI and thin clients, the security architect can ensure that the sensitive data is not stored in the conference rooms, but rather in a secure data center or cloud. The thin clients can also be easily managed and updated centrally, reducing the maintenance costs and risks. References: https://www.acecloudhosting.com/blog/what-is-vdi-thin-client/
https://www.acecloudhosting.com/blog/what-is-vdi-thin-client/  https://www.parallels.com/blogs/ras/vdi-thin-client/
https://www.parallels.com/blogs/ras/vdi-thin-client/
NEW QUESTION 13
A company is switching to a remote work model for all employees. All company and employee resources will be in the cloud. Employees must use their personal computers to access the cloud computing environment. The company will manage the operating system. Which of the following deployment models is the company implementing?
- A. CYOD
- B. MDM
- C. COPE
- D. VDI
Answer: D
Explanation:
According to Professor Messer’s video1, VDI stands for Virtual Desktop Infrastructure and it is a deploy model where employees use their personal computers to access a virtual machine that runs the company’s operating system and applications.
In the scenario described, the company is implementing a virtual desktop infrastructure (VDI) deployment model [1]. This allows employees to access the cloud computing environment using their personal computers, while the company manages the operating system. The VDI model is suitable for remote work scenarios because it provides secure and centralized desktop management, while allowing employees to access desktops from any device.
NEW QUESTION 14
Which of the following would help ensure a security analyst is able to accurately measure the overall risk to an organization when a new vulnerability is disclosed?
- A. A full inventory of all hardware and software
- B. Documentation of system classifications
- C. A list of system owners and their departments
- D. Third-party risk assessment documentation
Answer: A
Explanation:
A full inventory of all hardware and software would help ensure a security analyst is able to accurately measure the overall risk to an organization when a new vulnerability is disclosed, as it would allow the analyst to identify which systems and applications are affected by the vulnerability and prioritize the remediation efforts accordingly. A full inventory would also help the analyst to determine the impact and likelihood of a successful exploit, as well as the potential loss of confidentiality, integrity and availability of the data and services. References: https://www.professormesser.com/security-plus/sy0-601/sy0-601-video/risk-analysis/
https://www.professormesser.com/security-plus/sy0-601/sy0-601-video/risk-analysis/ https://www.comptia.org/landing/securityplus/index.html
https://www.comptia.org/landing/securityplus/index.html https://www.comptia.org/blog/complete-guide-to-risk-management
https://www.comptia.org/blog/complete-guide-to-risk-management
NEW QUESTION 15
A security analyst receives a SIEM alert that someone logged in to the app admin test account, which is only used for the early detection of attacks. The security analyst then reviews the following application log: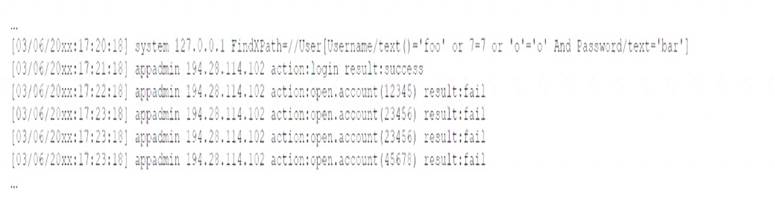
Which of the following can the security analyst conclude?
- A. A replay attack is being conducted against the application.
- B. An injection attack is being conducted against a user authentication system.
- C. A service account password may have been changed, resulting in continuous failed logins within the application.
- D. A credentialed vulnerability scanner attack is testing several CVEs against the application.
Answer: A
Explanation:
A replay attack is a type of network attack where an attacker captures and retransmits a valid data transmission, such as a login request, to gain unauthorized access or impersonate a legitimate user. In this case, the attacker may have captured the credentials of the app admin test account and used them to log in to the application. The application log shows multiple failed login attempts from different IP addresses, which indicates a replay attack.
NEW QUESTION 16
Which of the following would be most effective to contain a rapidly spreading attack that is affecting a large number of organizations?
- A. Machine learning
- B. DNS sinkhole
- C. Blocklist
- D. Honey pot
Answer: B
Explanation:
A DNS sinkhole would be most effective to contain a rapidly spreading attack that is affecting a large number of organizations. A DNS sinkhole is a technique that involves redirecting malicious or unwanted domain names to an alternative IP address, such as a black hole, a honeypot, or a warning page. A DNS sinkhole can help to prevent or disrupt the communication between infected systems and command-and-control servers, malware distribution sites, phishing sites, or botnets. A DNS sinkhole can also help to identify and isolate infected systems by monitoring the traffic to the sinkhole IP address. References: https://www.comptia.org/blog/what-is-a-dns-sinkhole
https://www.certblaster.com/wp-content/uploads/2020/11/CompTIA-Security-SY0-601-Exam-Objectives-1.0.pd
NEW QUESTION 17
A wet-known organization has been experiencing attacks from APTs. The organization is concerned that custom malware is being created and emailed into the company or installed on USB stocks that are dropped in parking lots. Which of the following is the best defense against this scenario?
- A. Configuring signature-based antivirus to update every 30 minutes
- B. Enforcing S/MIME for email and automatically encrypting USB drives upon assertion
- C. Implementing application execution in a sandbox for unknown software
- D. Fuzzing new files for vulnerabilities if they are not digitally signed
Answer: C
Explanation:
Implementing application execution in a sandbox for unknown software is the best defense against this scenario. A sandbox is a isolated environment that can run applications or code without affecting or being affected by other processes or systems. A sandbox can prevent malicious software from accessing or modifying sensitive data or resources, as well as limit its network communication and system privileges. A sandbox can also monitor and analyze the behavior and output of unknown software to determine if it is benign or malicious.
NEW QUESTION 18
Which of the following would be used to find the most common web-applicalion vulnerabilities?
- A. OWASP
- B. MITRE ATT&CK
- C. Cyber Kill Chain
- D. SDLC
Answer: A
Explanation:
OWASP (Open Web Application Security Project) is a non-profit organization that provides resources and guidance for improving the security of web applications. It publishes a list of the most common web application vulnerabilities, such as injection, broken authentication, cross-site scripting, etc., and provides recommendations and best practices for preventing and mitigating them
NEW QUESTION 19
......
100% Valid and Newest Version SY0-601 Questions & Answers shared by Certleader, Get Full Dumps HERE: https://www.certleader.com/SY0-601-dumps.html (New 534 Q&As)
