Exam Code: SY0-601 (Practice Exam Latest Test Questions VCE PDF)
Exam Name: CompTIA Security+ Exam
Certification Provider: CompTIA
Free Today! Guaranteed Training- Pass SY0-601 Exam.
Online CompTIA SY0-601 free dumps demo Below:
NEW QUESTION 1
A security administrator has discovered that workstations on the LAN are becoming infected with malware.
The cause of the infections appears to be users receiving phishing emails that are bypassing the current
email-filtering technology. As a result, users are being tricked into clicking on malicious URLs, as no internal controls currently exist in the environment to evaluate their safety. Which of the following would be BEST to implement to address the issue?
- A. Forward proxy
- B. HIDS
- C. Awareness training
- D. A jump server
- E. IPS
Answer: C
Explanation:
:
Awareness training should be implemented to educate users on the risks of clicking on malicious URLs. References: CompTIA Security+ Study Guide: Exam SY0-601, Chapter 9
NEW QUESTION 2
Which of the following security controls s sed to isolate a section of the network and its externally available resources from the internal corporate network in order to reduce the number of possible attacks?
- A. Faraday cages
- B. Air gap
- C. Vaulting
- D. Proximity readers
Answer: B
Explanation:
An air gap is a security measure that physically isolates a section of the network from any other network or device that could compromise its security. An air gap prevents any unauthorized access, data leakage, or malware infection through network connections, such as Ethernet cables, wireless signals, or Bluetooth
devices. An air gap can be used to protect sensitive or critical systems and data from external threats, such as hackers, spies, or cyberattacks.
NEW QUESTION 3
A systems integrator is installing a new access control system for a building. The new system will need to connect to the Company's AD server In order to validate current employees. Which of the following should the systems integrator configure to be the most secure?
- A. HTTPS
- B. SSH
- C. SFTP
- D. LDAPS
Answer: D
Explanation:
LDAPS (Lightweight Directory Access Protocol Secure) is the most secure protocol to use for connecting to an Active Directory server, as it encrypts the communication between the client and the server using SSL/TLS. This prevents eavesdropping, tampering, or spoofing of the authentication and authorization data.
References: 1
CompTIA Security+ Certification Exam Objectives, page 13, Domain 3.0: Implementation,
Objective 3.2: Implement secure protocols 2
CompTIA Security+ Certification Exam Objectives, page 15,
Domain 3.0: Implementation, Objective 3.5: Implement secure authentication mechanisms 3
https://docs.microsoft.com/en-us/previous-versions/windows/it-pro/windows-server-2008-R2-and-2008/cc731
NEW QUESTION 4
A security analyst reviews web server logs and notices the following line: 104.35. 45.53 [22/May/2020:07 : 00:58 +0100] "GET . UNION ALL SELECT
user login, user _ pass, user email from wp users—— HTTP/I.I" 200 1072
http://www.example.com/wordpress/wp—admin/
Which of the following vulnerabilities is the attacker trying to exploit?
- A. SSRF
- B. CSRF
- C. xss
- D. SQLi
Answer: D
Explanation:
SQLi stands for SQL injection, which is a type of web security vulnerability that allows an attacker to execute malicious SQL statements on a database server. SQLi can result in data theft, data corruption, denial of service, or remote code execution.
The attacker in the web server log is trying to exploit a SQLi vulnerability by sending a malicious GET request that contains a UNION ALL SELECT statement. This statement is used to combine the results of two or more SELECT queries into a single result set. The attacker is attempting to retrieve user login, user pass, and user email from the wp users table, which is a WordPress database table that stores user information. The attacker may use this information to compromise the WordPress site or the users’ accounts.
NEW QUESTION 5
Which of the following exercises should an organization use to improve its incident response process?
- A. Tabletop
- B. Replication
- C. Failover
- D. Recovery
Answer: A
Explanation:
A tabletop exercise is a type of simulation exercise that involves discussing hypothetical scenarios and testing the incident response plan in a low-stress environment. A tabletop exercise can help an organization to improve its incident response process by identifying gaps, weaknesses, roles, responsibilities, communication channels, etc., and by evaluating the effectiveness and efficiency of the plan.
NEW QUESTION 6
A user's laptop constantly disconnects from the Wi-Fi network. Once the laptop reconnects, the user can reach the internet but cannot access shared folders or other network resources. Which of the following types of attacks is the user MOST likely experiencing?
- A. Bluejacking
- B. Jamming
- C. Rogue access point
- D. Evil twin
Answer: D
Explanation:
An evil twin attack is when an attacker sets up a fake Wi-Fi network that looks like a legitimate network, but is designed to capture user data that is sent over the network. In this case, the user's laptop is constantly disconnecting and reconnecting to the Wi-Fi network, indicating that it is connecting to the fake network instead of the legitimate one. Once the user connects to the fake network, they are unable to access shared folders or other network resources, as those are only available on the legitimate network.
NEW QUESTION 7
Developers are writing code and merging it into shared repositories several times a day. where it is tested automatically. Which of the following concepts does this best represent?
- A. Functional testing
- B. Stored procedures
- C. Elasticity
- D. Continuous Integration
Answer: D
Explanation:
Continuous Integration is the concept that best represents developers writing code and merging it into shared repositories several times a day, where it is tested automatically. Continuous Integration is a software development practice that involves integrating code changes from multiple developers into a shared repository frequently and running automated tests to ensure quality and functionality. Continuous Integration can help to detect and fix errors early, improve collaboration, reduce rework, and accelerate delivery. References: https://www.comptia.org/blog/what-is-devops
https://www.certblaster.com/wp-content/uploads/2020/11/CompTIA-Security-SY0-601-Exam-Objectives-1.0.pd
NEW QUESTION 8
An organization relies on third-party videoconferencing to conduct daily business. Recent security changes
now require all remote workers to utilize a VPN to corporate resources Which of the following would best maintain high-quality videoconferencing while minimizing latency when connected to the VPN?
- A. Using geographic diversity lo have VPN terminators closer to end users
- B. Utilizing split tunneling so only traffic for corporate resources is encrypted
- C. Purchasing higher bandwidth connections to meet the increased demand
- D. Configuring OoS properly on the VPN accelerators
Answer: B
Explanation:
Utilizing split tunneling so only traffic for corporate resources is encrypted would best maintain high-quality videoconferencing while minimizing latency when connected to the VPN. Split tunneling is a technique that allows a VPN user to access both the public internet and the private network simultaneously, without routing all traffic through the VPN. This can improve the performance and quality of videoconferencing applications that rely on low latency and high bandwidth, as well as reduce the load on the VPN server.
NEW QUESTION 9
The spread of misinformation surrounding the outbreak of a novel virus on election day led to eligible voters choosing not to take the risk of going the polls. This is an example of:
- A. prepending.
- B. an influence campaign.
- C. a watering-hole attack.
- D. intimidation.
- E. information elicitation.
Answer: B
Explanation:
This scenario describes an influence campaign, where false information is spread to influence or manipulate people's beliefs or actions. In this case, the misinformation led eligible voters to avoid polling places, which influenced the outcome of the election.
NEW QUESTION 10
An incident has occurred in the production environment.
Analyze the command outputs and identify the type of compromise.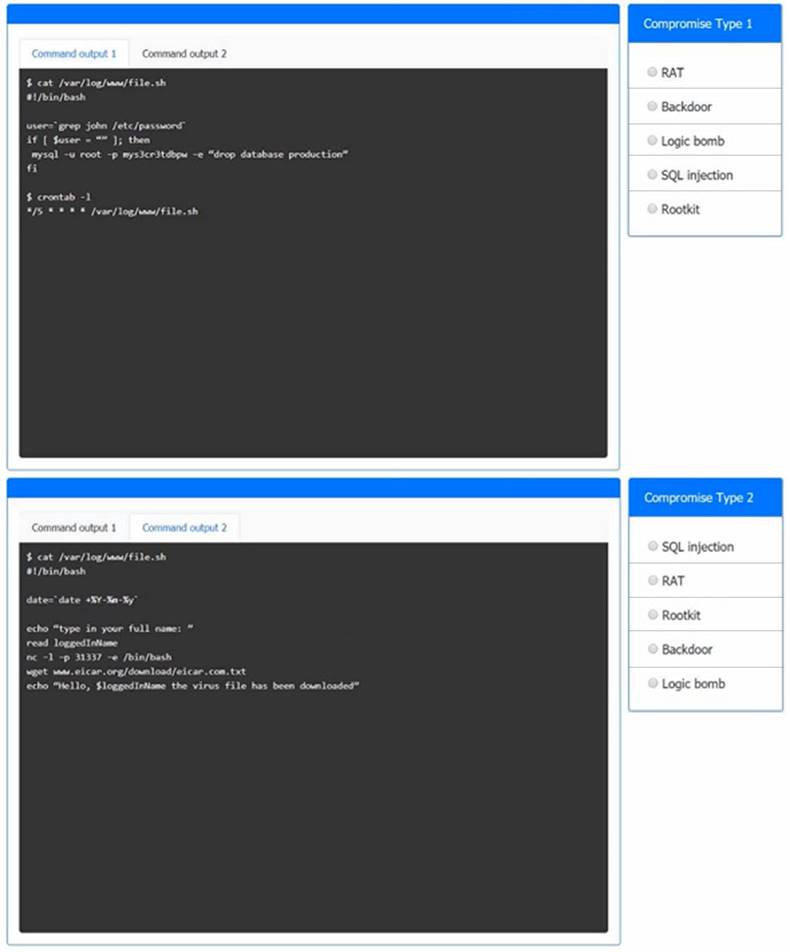
Solution:
Command Output1 = Logic Bomb
A logic bomb is a type of malicious code that executes when certain conditions are met, such as a specific date or time, or a specific user action1. In this case, the logic bomb is a script that runs every minute and checks if there is a user named john in the /etc/password file. If there is, it drops the production database using a MySQL command3. This could cause severe damage to the system and the data.
To prevent logic bombs, you should use antivirus software that can detect and remove malicious code, and also perform regular backups of your data. You should also avoid opening suspicious attachments or links from unknown sources, and use strong passwords for your accounts1.
Command Output2 = backdoorA backdoor is a type of malicious code that allows an attacker to access a system or network remotely, bypassing security measures1. In this case, the backdoor is a script that runs every time the date command is executed and prompts the user to enter their full name. Then, it opens a reverse shell connection using the nc command and downloads a virus file from a malicious website using the wget command2. This could allow the attacker to execute commands on the system and infect it with malware.
To prevent backdoors, you should use antivirus software that can detect and remove malicious code, and also update your system and applications regularly. You should also avoid executing unknown commands or scripts from untrusted sources, and use firewall rules to block unauthorized connections
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 11
Which of the following security concepts should an e-commerce organization apply for protection against erroneous purchases?
- A. Privacy
- B. Availability
- C. Integrity
- D. Confidentiality
Answer: C
Explanation:
Integrity is a security concept that ensures that data is accurate, complete and consistent, and that it has not been tampered with or modified in an unauthorized or unintended way. Integrity is important for e-commerce organizations to protect against erroneous purchases, as it can prevent data corruption, duplication, loss or manipulation that could affect the transactions or the records of the customers. Integrity can be achieved by using methods such as hashing, digital signatures, checksums, encryption and access control. Verified References: Security+ (Plus) Certification | CompTIA IT Certifications https://www.comptia.org/certifications/security (See What Skills Will You Learn?)
Security+ (Plus) Certification | CompTIA IT Certifications https://www.comptia.org/certifications/security (See What Skills Will You Learn?) CompTIA Security+ 601 - Infosec
CompTIA Security+ 601 - Infosec
https://www.infosecinstitute.com/wp-content/uploads/2021/03/CompTIA-Security-eBook.pdf (See Security+: 5 in-demand cybersecurity skills) CompTIA Security+ SY0-601 Certification Study Guide https://www.comptia.org/training/books/security-sy0-601-study-guide (See Chapter 1: Threats, Attacks and Vulnerabilities, Section 1.4: Cryptography and PKI)
CompTIA Security+ SY0-601 Certification Study Guide https://www.comptia.org/training/books/security-sy0-601-study-guide (See Chapter 1: Threats, Attacks and Vulnerabilities, Section 1.4: Cryptography and PKI)
NEW QUESTION 12
The Chief Executive Officer announced a new partnership with a strategic vendor and asked the Chief Information Security Officer to federate user digital identities using SAML-based protocols. Which of the following will this enable?
- A. SSO
- B. MFA
- C. PKI
- D. OLP
Answer: A
Explanation:
Federating user digital identities using SAML-based protocols enables Single Sign-On (SSO), which allows users to log in once and access multiple applications without having to enter their credentials for each one. References: CompTIA Security+ Certification Exam Objectives 1.3: Explain authentication and access controls.
CompTIA Security+ Certification Exam Objectives 1.3: Explain authentication and access controls.  CompTIA Security+ Study Guide, Sixth Edition, pages 41-42
CompTIA Security+ Study Guide, Sixth Edition, pages 41-42
NEW QUESTION 13
An upcoming project focuses on secure communications and trust between external parties. Which of the following security components will need to be considered to ensure a chosen trust provider IS
used and the selected option is highly scalable?
- A. Self-signed certificate
- B. Certificate attributes
- C. Public key Infrastructure
- D. Domain validation
Answer: C
Explanation:
PKI is a security technology that enables secure communication between two parties by using cryptographic functions. It consists of a set of components that are used to create, manage, distribute, store, and revoke digital certificates. PKI provides a secure way to exchange data between two parties, as well as a trust provider to ensure that the data is not tampered with. It also helps to create a highly scalable solution, as the same certificate can be used for multiple parties.
According to the CompTIA Security+ Study Guide, “PKI is a technology used to secure communications between two external parties. PKI is based on the concept of digital certificates, which are used to authenticate the sender and recipient of a message. PKI provides a trust provider to ensure that the digital certificate is valid and has not been tampered with. It also provides a scalable solution, as multiple parties can use the same certificate.”
NEW QUESTION 14
A company purchased cyber insurance to address items listed on the risk register. Which of the following strategies does this represent?
- A. Accept
- B. Transfer
- C. Mitigate
- D. Avoid
Answer: B
Explanation:
A company purchased cyber insurance to address items listed on the risk register. This represents a transfer strategy. A transfer strategy involves transferring or sharing some or all of the responsibility or impact of a risk to another party, such as an insurer, a supplier, or a partner. A transfer strategy can help to reduce the financial liability or exposure of the company in case of a security incident or breach. References: https://www.comptia.org/blog/what-is-cyber-insurance
https://www.certblaster.com/wp-content/uploads/2020/11/CompTIA-Security-SY0-601-Exam-Objectives-1.0.pd
NEW QUESTION 15
An analyst is working on an investigation with multiple alerts for multiple hosts. The hosts are showing signs of being compromised by a fast-spreading worm. Which of the following should be the next step in order to stop the spread?
- A. Disconnect every host from the network.
- B. Run an AV scan on the entire
- C. Scan the hosts that show signs of
- D. Place all known-infected hosts on an isolated network
Answer: D
Explanation:
Placing all known-infected hosts on an isolated network is the best way to stop the spread of a worm infection. This will prevent the worm from reaching other hosts on the network and allow the infected hosts to be cleaned and restored. Disconnecting every host from the network is not practical and may disrupt business operations. Running an AV scan on the entire network or scanning the hosts that show signs of infection may not be effective or fast enough to stop a fast-spreading worm.
NEW QUESTION 16
A software company adopted the following processes before releasing software to production
• Peer review
• Static code scanning
• Signing
A considerable number of vulnerabilities are still being detected when code is executed on production Which of the following security tools can improve vulnerability detection on this environment?
- A. File integrity monitoring for the source code
- B. Dynamic code analysis tool
- C. Encrypted code repository
- D. Endpoint detection and response solution
Answer: B
Explanation:
A dynamic code analysis tool is a security tool that can improve vulnerability detection on this environment by testing and analyzing the software during runtime. Dynamic code analysis can identify potential vulnerabilities, errors, or performance issues that may not be visible in the source code or during static analysis, such as memory leaks, buffer overflows, or input validation errors. Dynamic code analysis can also simulate real-world scenarios and user inputs to evaluate the behavior and functionality of the software
NEW QUESTION 17
An attacker is targeting a company. The attacker notices that the company’s employees frequently access a particular website. The attacker decides to infect the website with malware and hopes the employees’ devices will also become infected. Which of the following techniques is the attacker using?
- A. Watering-hole attack
- B. Pretexting
- C. Typosquatting
- D. Impersonation
Answer: A
Explanation:
a watering hole attack is a form of cyberattack that targets a specific group of users by infecting websites that they commonly visit123. The attacker seeks to compromise the user’s computer and gain access to the network at the user’s workplace or personal data123. The attacker observes the websites often visited by the victim or the group and infects those sites with malware14. The attacker may also lure the user to a malicious 4site. A watering hole attack is difficult to diagnose and poses a significant threat to websites and users2 .
NEW QUESTION 18
A company wants to enable BYOD for checking email and reviewing documents. Many of the documents contain sensitive organizational information. Which of the following should be deployed first before allowing the use of personal devices to access company data?
- A. MDM
- B. RFID
- C. DLR
- D. SIEM
Answer: A
Explanation:
MDM stands for Mobile Device Management, which is a solution that can be used to manage and secure personal devices that access company data. MDM can enforce policies and rules, such as password protection, encryption, remote wipe, device lock, application control, and more. MDM can help a company enable BYOD (Bring Your Own Device) while protecting sensitive organizational information.
NEW QUESTION 19
......
Recommend!! Get the Full SY0-601 dumps in VCE and PDF From Certleader, Welcome to Download: https://www.certleader.com/SY0-601-dumps.html (New 534 Q&As Version)
